TradeChain allows the incorporation of intelligent assets into the built environment goes beyond improving energy efficiency. It is reshaping both asset utilization and material management within the sector.
TradeChain connects infrastructures components to enable the wider use of performance contracts and predictive maintenance schemes while at the same time dramatically increasing the potential for improved asset utilization through sharing.
TradeChain entails a built environment that is flexible and modifiable and which, through its interconnectivity, can feed wider systems (the city or the traffic grid) with information that enhances both traffic management and urban planning.
TradeChain Intelligent Assets allows building service providers and construction companies that are already using IoT to optimize the energy efficiency of buildings and larger communal systems (such as street lighting). Large building service providers, such as Johnson Controls and Honeywell, use IoT to help the tenants of their buildings to reduce the cost of their energy bills, while enabling utilities providers to better plan their energy production and avoid wasteful peaks
TradeChain is changing how materials are maintained and reused In a more novel approach, intelligent assets are now increasingly being deployed to address the sources of waste and resource inefficiencies at several stages across an asset’s use cycle.
TradeChain allows knowing the location of building components as well as their condition gives asset owners unprecedented monitoring capabilities, enabling both new business and financial models.
TradeChain fosters models to enable extended use cycles of buildings as well as improved potential to loop or cascade building components and materials in new use cycles at the end of the infrastructure components use
Distributed registration -analogy between LEDGER and DISTRIBUTED LEDGER- "democratizes" the identification, authentication and transparency of transactions through "peer-to-peer between validation" without third party intermediation. Who dominates BlockChain... will dominate the "Rules of Trust" since BlockChain technology eliminates the need for a third party to establish connections with each other.
All have the same information, therefore, the rules of trust are validated by the community itself, guaranteeing the security, transparency and reliability of any transaction.
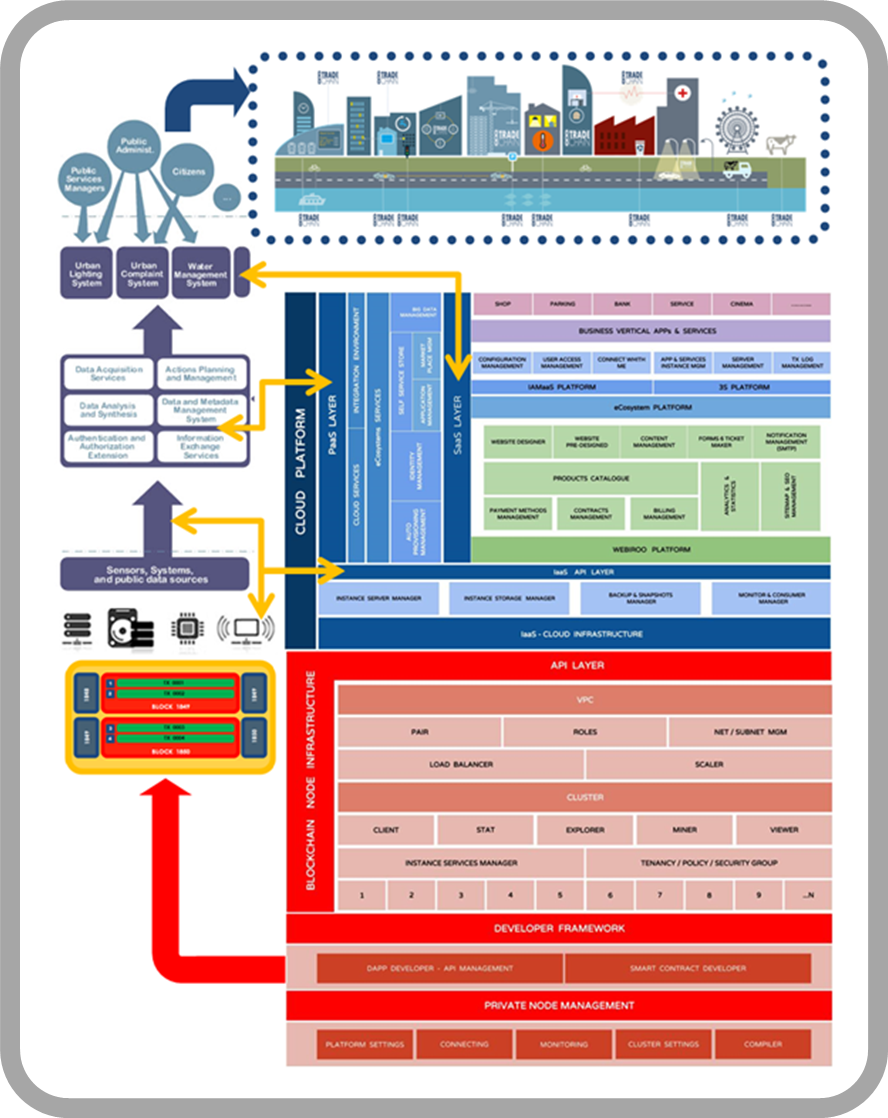
In order to the kind of exploitation and application of the BlockChain Model, the focal point is the management and control of NODES. Therefore, the Platform provides the ability to create and manage Own Infrastructures and deploy distributed applications that allow executing transactions dependent on smart rules
Having control of the NODE gives us substantial advantages. The most relevant ones: It acts as Account Admin, therefore it allows us to control the list of public keys managed by our activity. Although the content is cryptographic and there is no possibility of access, only who has the privilege of Account Admin is the one who can authenticate and therefore sign the transaction. Later the consensus of the Community will be in charge of validating it at time of mining of the Block. It allows us to run the Ethereum Stat and Last Block reports displaying the activity of the filtered BlockChain Net.
It means that it offers us the possibility of monitoring the activity of our nodes in a detailed way and being able to deliver the same view to our clients. It allows us to distribute processes between NODES
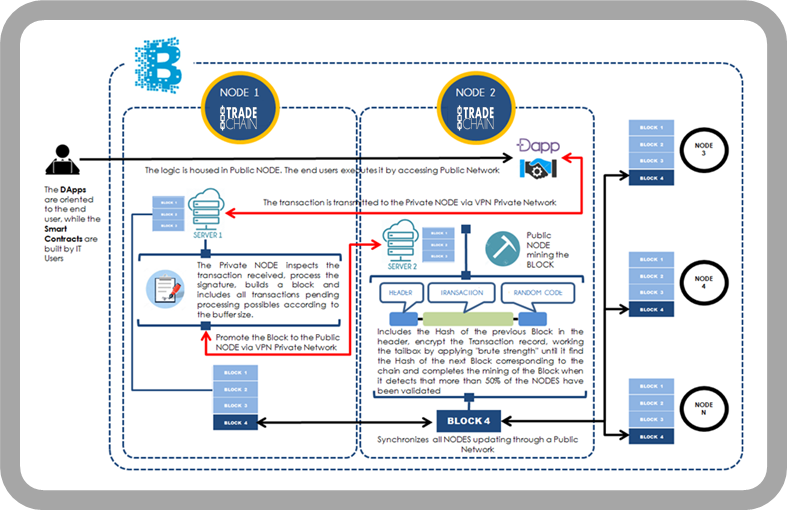
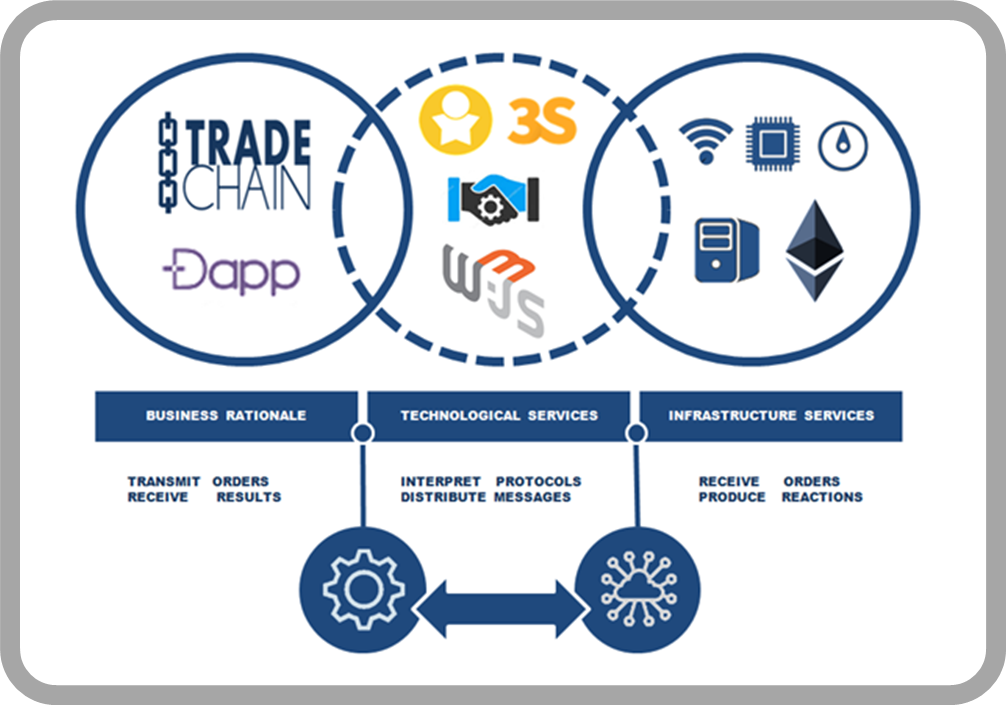
The main settlement is based on Development of Business Logic through distributed applications (DApps) -which allow to establish a communication interface with the End User- and Smart Contracts -which allow to model the execution rules under the Action-Reaction principle-.
Unlike typical Apps that are centralized applications since the trust is deposited in a main entity -for instance, a server or a data bank- the DApps are decentralized applications, where trust is based on the community and are not controlled by any authority and neither require any other intermediary entity for working. They just need the chain of blocks to express themselves...
These are code capsules programmable, autonomous, self-operative, distributed all nodes, impossible to alter and therefore immutable. It means that it will always have the same behavior without requiring the action of a third party, in a predictable environment, transparent and incorruptible and that will be executed automatically when the specific conditions defined in itself are met.
Many of today’s infrastructure was designed and built in an analog era and built before it was possible to integrate sensors or to build better, more cost-effective energy, water, logistics or transport infrastructure and much before cars might talk to the road, or drive on their own Today everything that can be connected will be connected, as an ‘Internet of Things’ (IoT).
The key is the interconnection via the Internet of computing devices embedded in everyday objects, enabling them to send and receive data... "if one thing can prevent the Internet of things from transforming the way we live and work, it will be a breakdown in security"
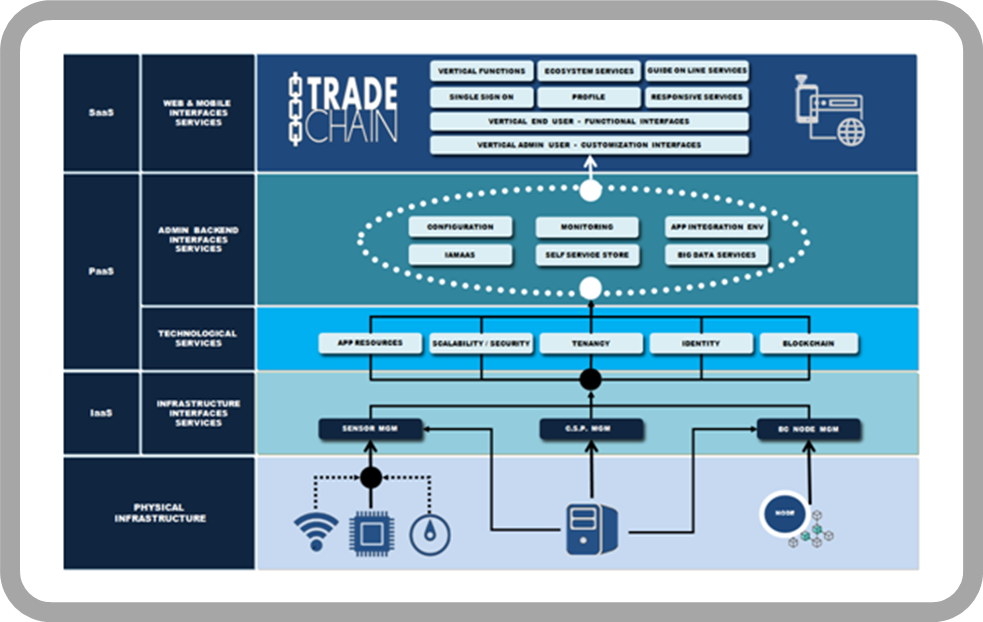
Cloud Computing PARADIGM has emerged disrupting traditional “Value Chains”, allowing unprecedents “economies of scale” and consolidating the ”techological democracy” concept to result of the eroding of “entry barriers” to ”state of the art” technology infrastructure
Cloud Technology has enabled the advent of the "Internet of Things", having understood that things themselves produce information, whose obtaining -by means of sensors, devices, etc.- and subsequent use produce results of maximum richness and direct impact on the processes optimization.
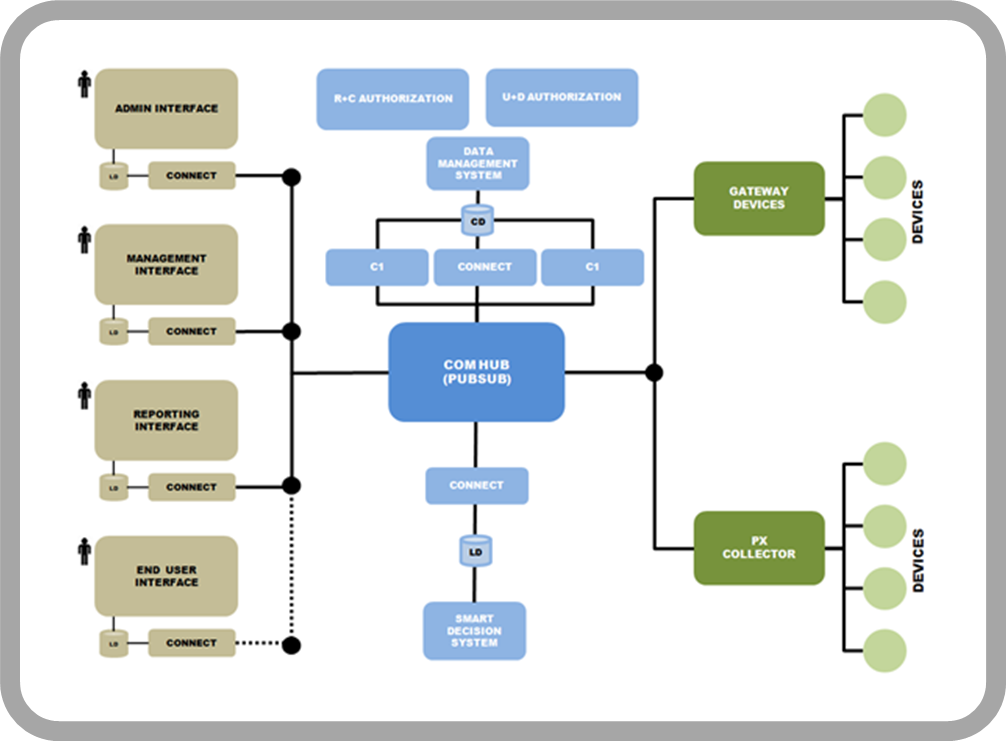
The ability to connect devices and interpret them means that IoT can have unlimited applications, can act in almost any area and be responsible for collecting information in multiple environments: from living beings and natural ecosystems to buildings and vehicles, so they could be used for any type of behavior monitoring, both environmental and urbanistic
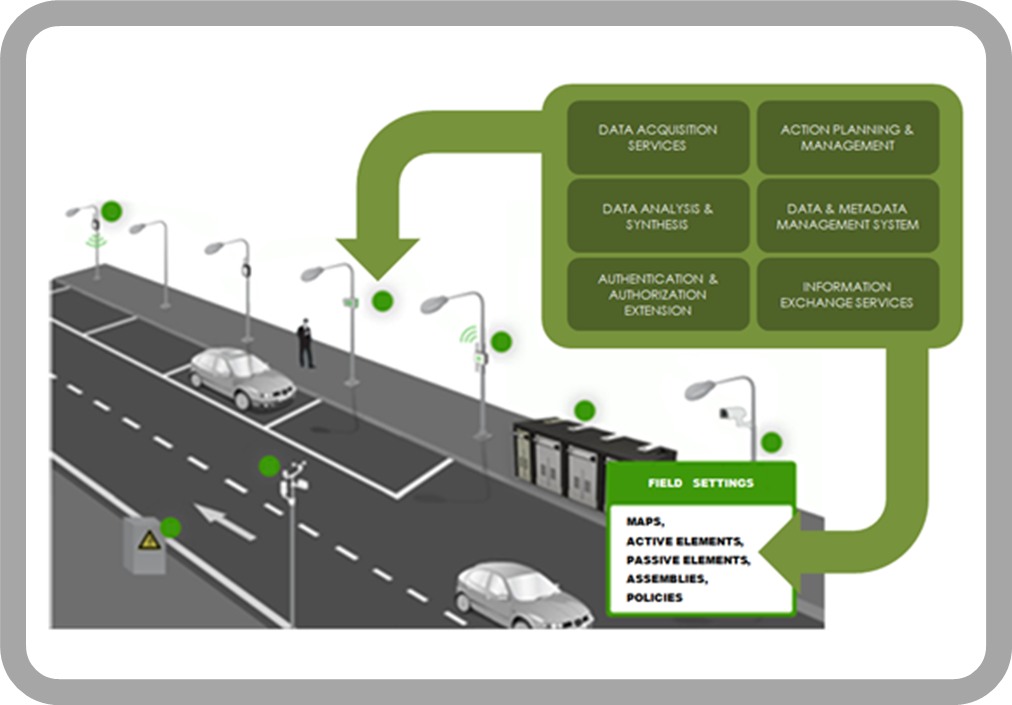
The key is "Permissioned access by users or system processes to the authenticated resources"
To identify oneself is to say who you are: In the case of interactions between human beings, if for example you knock on the door of a neighbor, to your question of "who is it?" You will answer with your name. You will be identifying
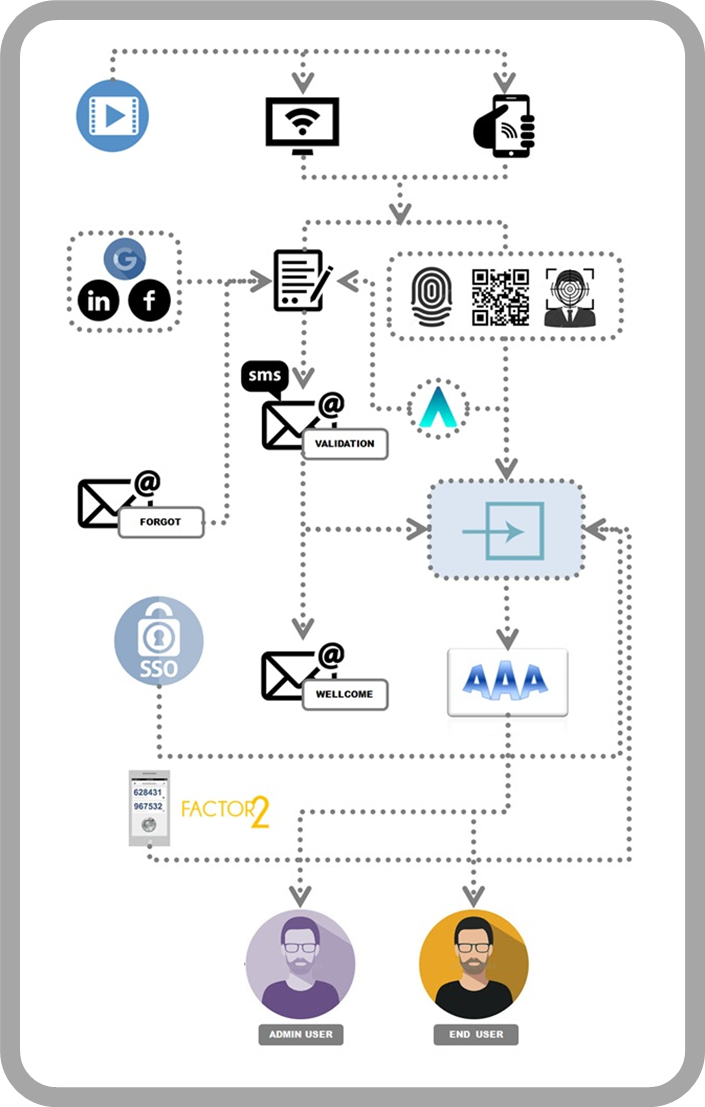
Authenticate is to show that you are who you say you are: When your neighbor looks through the peephole, your face will serve to authenticate you. He will know that you are who you say you are, because he will recognize you by your physical features. It will recognize your identity.
TradeChain solves througth its IAMaaS Services the Authentication, Authorization and Accounting process in a transparent way, administering the secure request/token/session rules until the complete satisfaction of the trust relationships is satisfied before allowing the requesting party to access the services, determining their capacity to consume resources, repositories and applications, based on the assignment and/or detection of profiles, roles, attributions and rules
Provides workshop-type tools to configure standardized policies, delegating to the rules engine the adaptation of the behavior of the Platform according to the declared parameters that allow defining situations and moments in which to implement the authorization control and access authorization
In this order, the Platform provides entire control of every your users and covering end-to-end chain of authentication, authorization and accounting to all apps from a single entry point and also, IAMaaS is the point of integration -interoperability- of new services to the Model, providing the interfaces so that the IT user can perform the complete management during the entire life cycle of any application.
The User can consult the information associated with the instance: URL, ID, provisioned services, security key, authorizations history, etc. User can also configure any parameter, assign or deassign resources: RAM, Caches, DDBB instances, etc ... available for a specific application or for a group of instances of a specific client
The key is to enable users to assess the risks inherent to supply chain participation by implementing different tiers of operations in accordance with documentation milestones compliance for each tier
Not only will verification processes be regulation-compliant but they will also be designed to keep the BlockChain-based financing processes streamlined.
This collection of data pertaining to individuals, companies and deals will be verified and periodically updated by multiple trusted parties. The records will be made persistently incorruptible and non- repudiable on the enterprise BlockChain with privacy control.